As cyber threats continue to evolve, so must the technologies that protect our data. One of the most significant upcoming threats is quantum computing, which has the potential to break traditional encryption schemes. To counter this, researchers and technologists are now merging modern data storage solutions with Post-Quantum Cryptography (PQC) to build a future-proof security architecture.
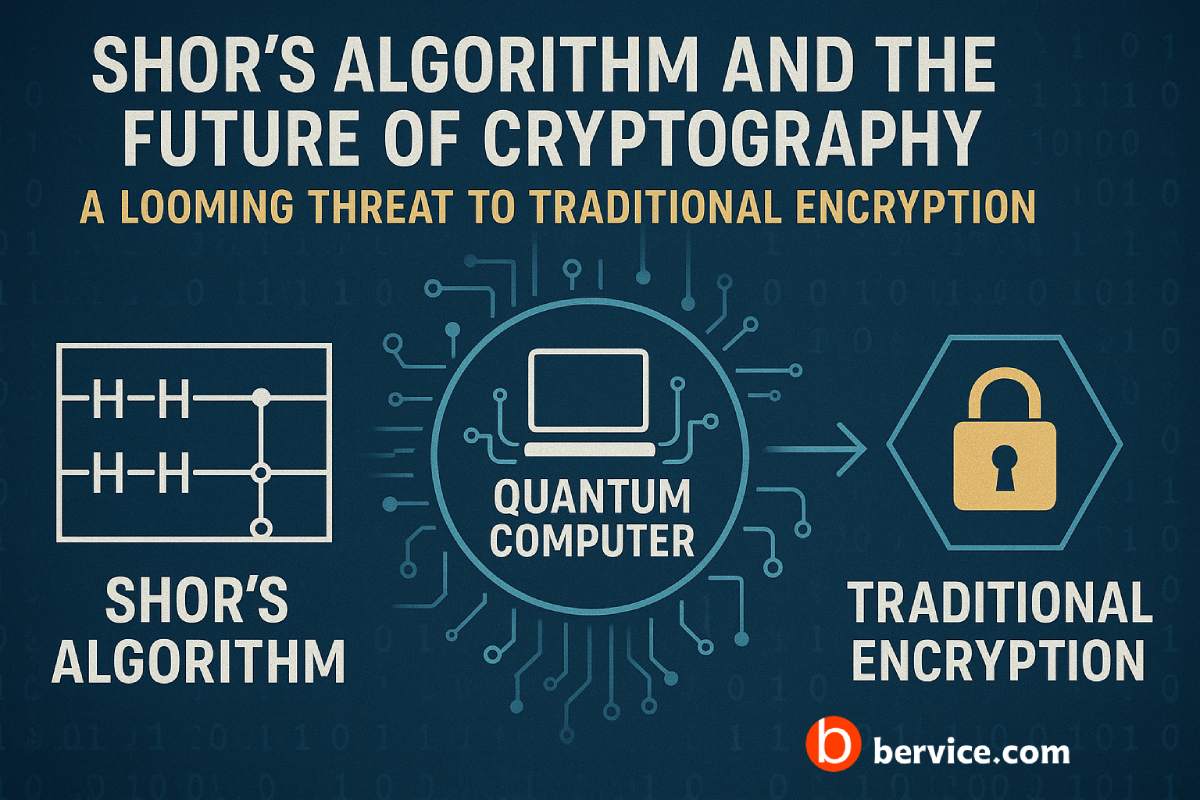
🚀 The Quantum Threat to Traditional Encryption
Most current encryption methods—such as RSA, ECC, and DSA—rely on the difficulty of mathematical problems like prime factorization or discrete logarithms. These are hard for classical computers to solve but can be efficiently broken by quantum algorithms, especially Shor’s algorithm.
This quantum advantage poses a serious risk to:
- Password protection
- Secure communications (TLS/SSL)
- Encrypted databases
- Blockchain systems
As a result, encrypted passwords and stored credentials could be decrypted by a powerful quantum computer, compromising user data at a global scale.
🧬 Post-Quantum Cryptography (PQC): A New Line of Defense
Post-Quantum Cryptography refers to cryptographic algorithms that are believed to be secure even against quantum computers. Developed by researchers worldwide and vetted by NIST’s standardization process, PQC algorithms are based on problems believed to be hard even for quantum machines, such as:
- Lattice-based problems (e.g., Kyber, Dilithium)
- Code-based problems (e.g., Classic McEliece)
- Multivariate polynomial equations
- Hash-based signatures
These algorithms are designed to replace RSA and ECC in existing systems, offering strong resistance against both classical and quantum attacks.
🗄️ Next-Gen Data Storage: Distributed, Encrypted, and Resilient
Modern data storage technologies have gone beyond traditional centralized systems to incorporate:
- 🌐 Decentralized storage (e.g., IPFS, Filecoin)
- ☁️ Cloud object storage with encryption (e.g., S3-compatible storage)
- ⚡ Zero-knowledge file systems
- 🧠 AI-driven storage management for adaptive access control
These solutions offer advantages like redundancy, fault tolerance, global accessibility, and better privacy. However, when combined with PQC, they provide end-to-end post-quantum-safe data protection.
🧩 Integration: PQC + Modern Storage
Here’s how PQC is being integrated into new-gen storage models:
- Quantum-Safe Password Hashing:
- Replacing traditional hashing algorithms (e.g., bcrypt, PBKDF2) with quantum-resistant KDFs.
- Using lattice-based hash functions for password storage.
- Encrypted File Systems with PQC Keys:
- Encrypting files and databases using symmetric keys secured with PQC-based public/private key pairs.
- Enabling secure key exchange using algorithms like Kyber.
- Multi-User Access & Key Sharing:
- Leveraging attribute-based encryption with PQC primitives for secure and auditable file sharing across organizations.
- Secure Cloud Syncing:
- Utilizing PQC signatures (e.g., Dilithium) to verify file integrity across nodes in decentralized networks.
🔐 Use Case Example
Scenario: A financial organization stores sensitive customer data on a decentralized cloud network. By encrypting this data using symmetric AES-256 and wrapping the keys with Kyber public keys, the system ensures:
- Resistance to quantum decryption
- Safe key distribution
- Long-term confidentiality of stored passwords and transactions
This dual-layered architecture significantly reduces the risk of data breaches due to future quantum threats.
🧭 Looking Ahead
By 2030, quantum computers may reach a level where they can break current encryption algorithms. The time to act is now.
✔ Transition to post-quantum-safe encryption
✔ Upgrade password storage methods
✔ Deploy modern, encrypted storage systems
✔ Audit your infrastructure for quantum vulnerabilities
🧠 Final Thoughts
The combination of post-quantum cryptography and next-generation storage systems marks a critical evolution in cybersecurity. This approach doesn’t just patch existing systems—it reinvents security from the ground up to be resilient in the quantum era.
🔐 Future-proof your data today. Because tomorrow’s threats need today’s innovation.
Connect with us : https://linktr.ee/bervice