As the horizon of quantum computing draws nearer, the year 2026 marks a pivotal moment in the cybersecurity and digital infrastructure landscape. Global enterprises, governments, and tech platforms are no longer just theorizing about quantum threats — they are actively transitioning their infrastructure to prepare for the post-quantum era. Post-Quantum Cryptography (PQC) is no longer a niche topic for cryptographers; it’s becoming a foundational element in digital resilience and platform security.
Why 2026 Is the Tipping Point
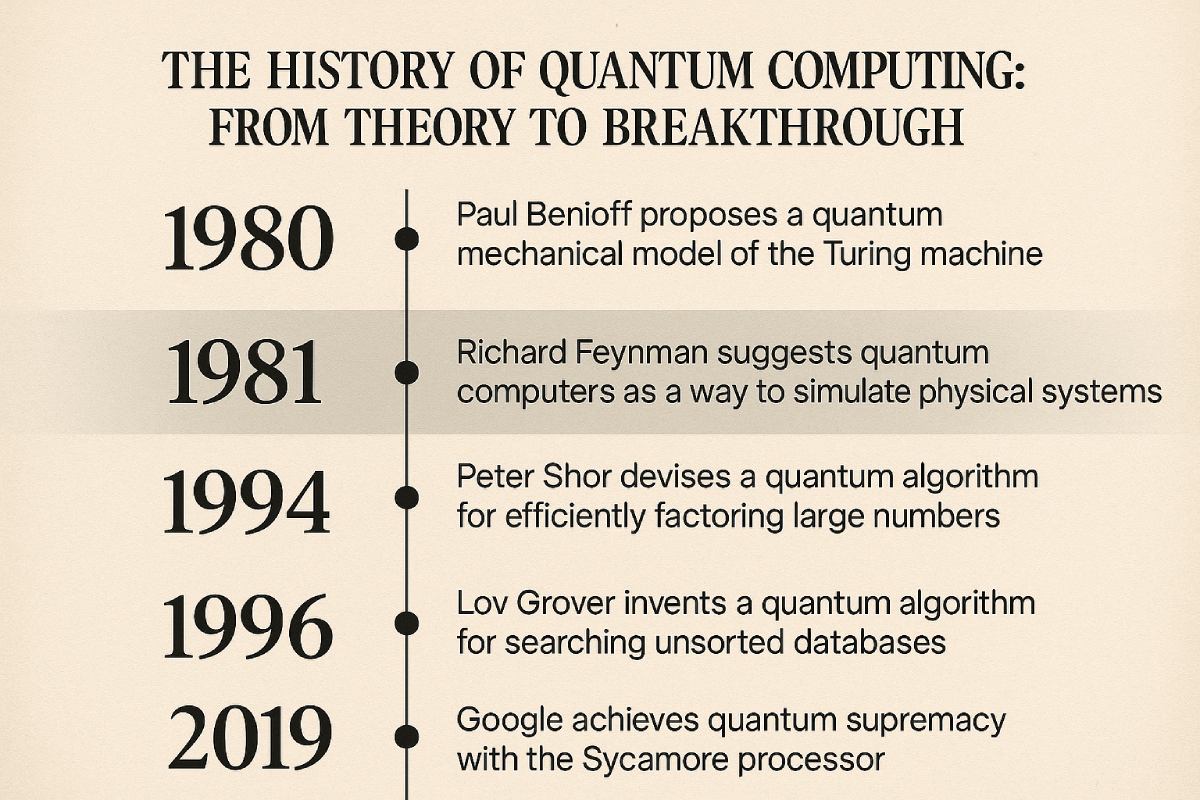
The accelerated pace of quantum computing development, led by advancements from tech giants and academic institutions, has reduced the timeline for practical quantum computers from decades to possibly a few short years. This urgency has turned 2026 into a wake-up call for infrastructure owners: legacy cryptographic algorithms like RSA and ECC, which underpin most digital communications today, are vulnerable to quantum attacks. The infamous Shor’s algorithm poses a real threat to public-key cryptography — making transition not optional but necessary.
As a result, governments such as the United States (through NIST), the European Union, and China are fast-tracking PQC initiatives, establishing compliance roadmaps, and encouraging early adoption. In tandem, companies are re-architecting systems, reevaluating encryption libraries, and adopting hybrid cryptographic models to ensure both classical and quantum-safe compatibility.
What is Post-Quantum Cryptography (PQC)?
Post-Quantum Cryptography refers to cryptographic algorithms designed to be secure against both classical and quantum computers. Unlike quantum cryptography, PQC does not require quantum hardware; it can be implemented using classical computing resources. Algorithms such as Kyber, Dilithium, Falcon, and SPHINCS+ are among the finalists in NIST’s standardization process, each offering varying trade-offs between performance, key sizes, and security levels.
These algorithms are based on mathematical problems believed to be hard for both classical and quantum computers, such as lattice-based, code-based, hash-based, and multivariate polynomial cryptography. Their implementation in real-world infrastructure is what 2026 is all about.
Infrastructure Overhaul: From Concept to Deployment
Transitioning to PQC is not merely a matter of swapping encryption libraries. It requires a deep audit of digital infrastructure, including:
- TLS/SSL and VPN protocols
- Blockchain systems and digital signatures
- IoT device firmware and lifecycle management
- Authentication and identity systems
- Secure email, messaging, and file storage
Organizations are building hybrid cryptographic stacks that combine classical and post-quantum algorithms to maintain interoperability while phasing in new security standards. Platforms like Google Chrome, Mozilla Firefox, and OpenSSH have already begun integrating PQC support. Major cloud providers, including AWS and Azure, are also piloting quantum-safe key exchanges and VPN tunnels.
In 2026, early adopters are setting the pace: financial institutions, defense systems, and blockchain platforms are actively hardening systems against “harvest-now, decrypt-later” attacks — where encrypted data is stolen today with the intent to decrypt it later using future quantum capabilities.
Challenges Ahead and the Path Forward
Despite rapid progress, the PQC transition is not without hurdles:
- Key sizes and performance: PQC algorithms often have larger keys and slower performance, which can strain mobile devices or low-bandwidth environments.
- Standardization delays: While NIST is finalizing its standards, the lack of universal adoption can create fragmentation.
- Backward compatibility: Ensuring systems can securely operate in both classical and quantum-resistant modes during the transition is a major design challenge.
To overcome these issues, 2026 will also see a rise in PQC-readiness frameworks, enterprise toolkits, and quantum risk assessment platforms. Collaboration between academia, governments, and tech enterprises will play a crucial role in education, deployment strategy, and global coordination.
Conclusion: A New Era of Digital Trust
2026 is not the year quantum computers break encryption — but it is the year organizations must act to prevent that eventuality. The shift to post-quantum cryptography is not just about future-proofing security; it’s about maintaining digital trust in a rapidly evolving threat landscape.
Forward-looking institutions that treat 2026 as their quantum-resilience milestone will not only protect their data but also lead the market in secure digital transformation. In a world approaching the quantum threshold, PQC isn’t optional — it’s inevitable.
Connect with us : https://linktr.ee/bervice