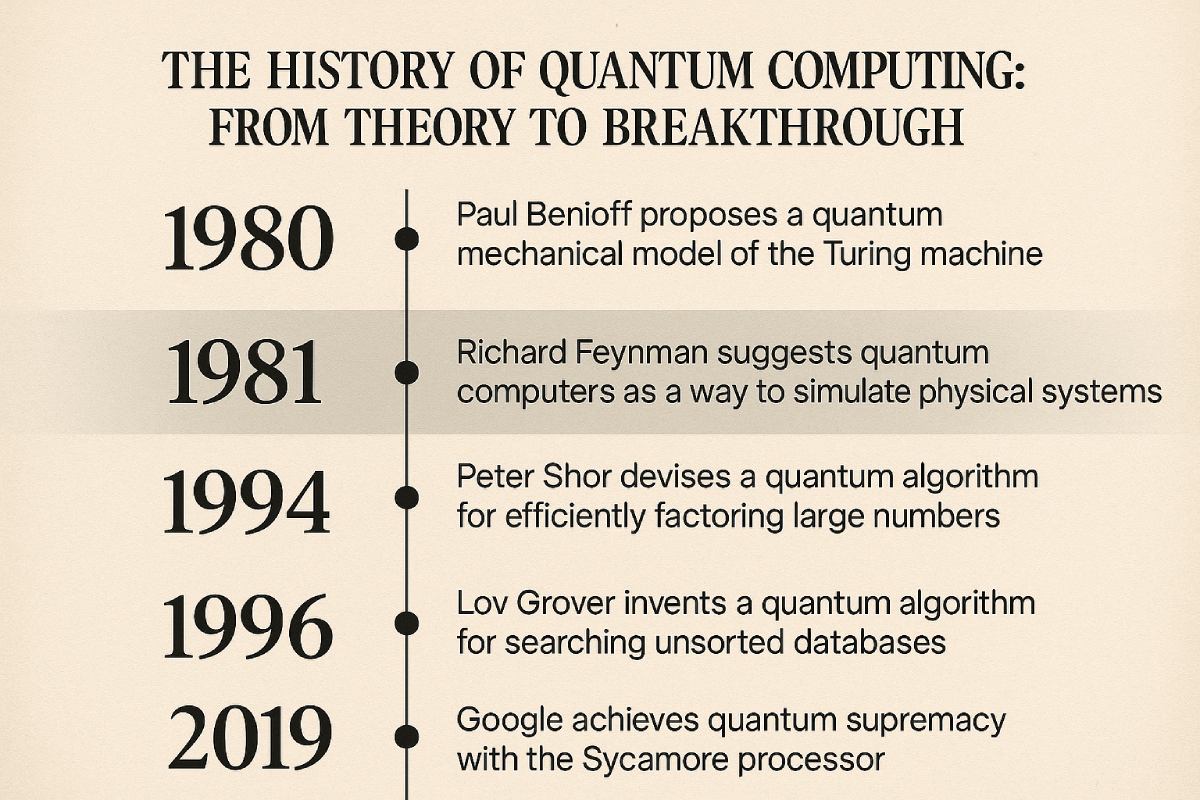
As the capabilities of quantum computers rapidly advance, the security of classical cryptographic systems faces an unprecedented threat. Post-Quantum Cryptography (PQC) emerges as a vital frontier in the effort to safeguard digital communication, data, and infrastructure from quantum-enabled attacks. This article explores what post-quantum cryptography is, why it matters, how it works, and the current state of global transition toward quantum-resistant security.
🌍 What Is Post-Quantum Cryptography?
Post-Quantum Cryptography refers to cryptographic algorithms that are designed to be secure against an adversary with access to a large-scale quantum computer. Unlike classical encryption methods—such as RSA, ECC (Elliptic Curve Cryptography), and DH (Diffie-Hellman)—which rely on problems like integer factorization and discrete logarithms, PQC algorithms are based on mathematical problems believed to remain hard even in the presence of quantum computing.
These quantum-resistant algorithms are intended to run on classical hardware, ensuring compatibility with existing systems while preparing for the post-quantum era.
⚠️ Why Is Post-Quantum Security Urgent?
Quantum computers, particularly those leveraging Shor’s algorithm, can efficiently solve problems that form the backbone of today’s public-key cryptography. For instance:
- RSA: Broken via fast integer factorization.
- ECC: Broken via solving the discrete logarithm problem.
- DH Key Exchange: Vulnerable to quantum eavesdropping.
Even though large-scale quantum computers are not yet widely available, the concept of “harvest now, decrypt later” presents a serious risk. Attackers can intercept encrypted data today and store it until quantum capabilities are sufficient to decrypt it. That’s why proactive transition to PQC is essential to ensure long-term confidentiality and future-proof digital assets.
🔐 Types of Post-Quantum Algorithms
PQC focuses on several mathematical problem domains that are believed to be quantum-resistant:
- Lattice-based cryptography (e.g., CRYSTALS-Kyber, CRYSTALS-Dilithium): Based on problems like Learning With Errors (LWE) and Shortest Vector Problem (SVP).
- Hash-based cryptography (e.g., SPHINCS+): Uses Merkle tree structures and is well-suited for digital signatures.
- Code-based cryptography (e.g., Classic McEliece): Relies on the difficulty of decoding general linear codes.
- Multivariate polynomial cryptography (e.g., Rainbow): Uses hard-to-solve polynomial equations over finite fields.
- Isogeny-based cryptography (e.g., SIKE – now considered broken): Based on hard problems in elliptic curve isogenies.
Each category offers trade-offs in terms of speed, key size, and computational cost. Lattice-based systems have emerged as strong candidates for standardization due to their balanced performance and security.
🛠️ Standardization and Global Efforts
Recognizing the urgency, the National Institute of Standards and Technology (NIST) launched a multi-year process to standardize PQC algorithms. In July 2022, NIST announced a set of finalists:
- CRYSTALS-Kyber (key encapsulation)
- CRYSTALS-Dilithium (digital signatures)
- SPHINCS+ (hash-based digital signatures)
- FALCON (compact and efficient signatures)
These algorithms are now undergoing rigorous testing, review, and optimization before becoming formal standards expected to be published in 2024–2025.
Global entities such as Google, IBM, and Cloudflare have already started integrating PQC into experimental TLS connections and VPN protocols to test performance and compatibility.
🔄 Challenges in Migration
Transitioning to post-quantum cryptography is not trivial. Key challenges include:
- Backward compatibility with legacy systems
- Increased key sizes and computational overhead
- Deployment logistics across the internet’s vast infrastructure
- Hybrid encryption models (classical + post-quantum) to ensure smooth migration
- Lack of public awareness and institutional preparedness
Despite these obstacles, failing to transition in time could result in catastrophic breaches once large-scale quantum computers arrive.
🧭 Looking Ahead
Post-Quantum Cryptography is not just a theoretical concern—it’s a critical step toward securing the digital world against emerging quantum threats. As quantum computing progresses from theory to reality, nations, companies, and developers must prioritize adopting PQC in software, hardware, and communications infrastructure.
Just like the Y2K problem prompted early adaptation, the quantum threat demands immediate attention, collaboration, and innovation. The race for cryptographic resilience has already begun, and those who prepare now will be the ones who stay secure in the quantum age.
Connect with us : https://linktr.ee/bervice