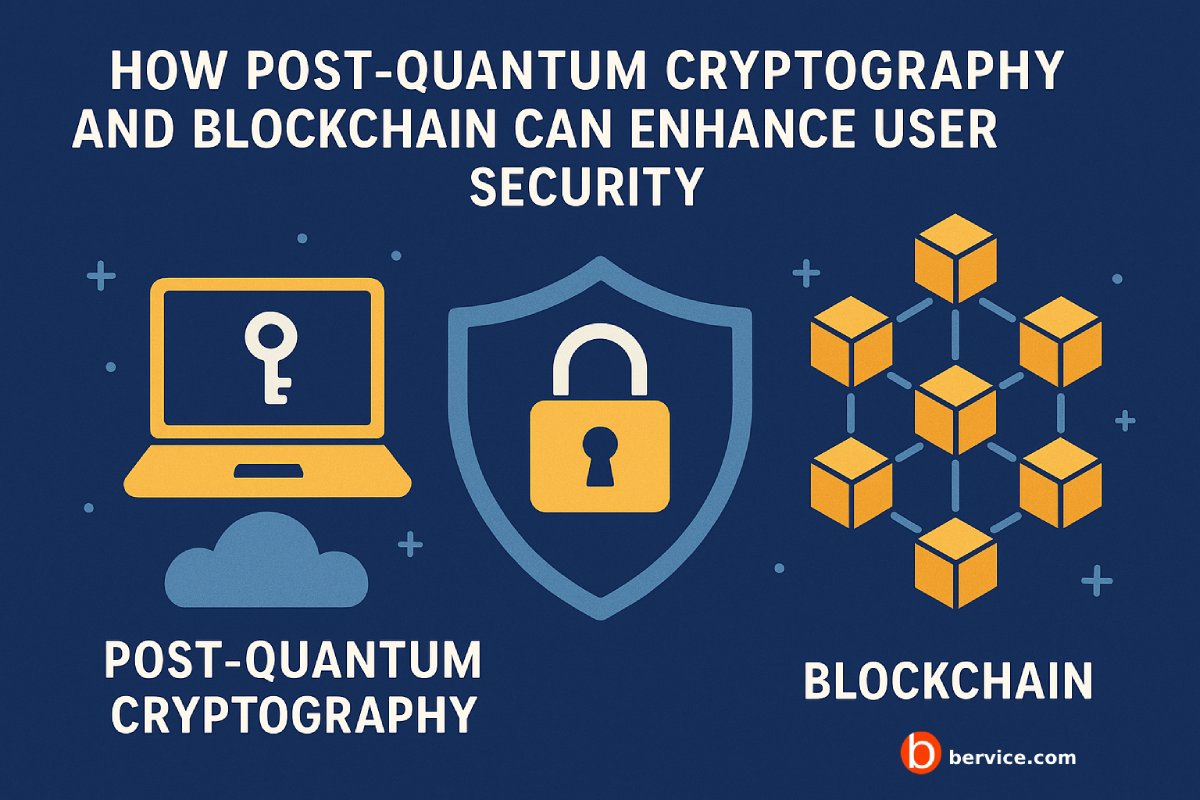
In an increasingly digital world, the threats to user privacy and security are evolving rapidly. Two revolutionary technologies—Post-Quantum Cryptography (PQC) and Blockchain—are emerging as critical tools to fortify digital security frameworks. When combined, they hold the potential to dramatically enhance user protection against both present-day cyberattacks and future quantum threats.
The Quantum Threat to Existing Cryptography
Traditional cryptographic systems, such as RSA and ECC (Elliptic Curve Cryptography), rely on mathematical problems that are currently infeasible for classical computers to solve efficiently. However, with the advent of quantum computers, algorithms like Shor’s algorithm could break these systems within minutes. This looming danger means that much of today’s encrypted internet traffic could be rendered vulnerable in the near future.
Post-Quantum Cryptography offers a robust solution. It consists of cryptographic algorithms that are resistant to both classical and quantum computing attacks. These include lattice-based, hash-based, code-based, and multivariate polynomial-based schemes. Importantly, PQC can be implemented using classical computing infrastructure, making it a practical transition strategy before quantum computers become mainstream.
Blockchain: A Decentralized Foundation for Security
Blockchain technology introduces a decentralized and tamper-resistant method of recording transactions and data. Each block in a chain contains a cryptographic hash of the previous block, a timestamp, and transaction data, forming an immutable ledger. This makes it ideal for ensuring transparency, traceability, and data integrity without needing a centralized authority.
The decentralized nature of blockchain also reduces single points of failure. Hackers would need to compromise a majority of nodes (over 51%) to alter data—an increasingly impractical task as networks grow. When users store sensitive information or make transactions on blockchain platforms, they are protected by cryptographic consensus mechanisms that offer a much higher standard of security than traditional systems.
The Convergence: PQC + Blockchain = Future-Proof Security
While blockchain is inherently secure against classical attacks, it is not immune to quantum threats. Many current blockchain systems rely on elliptic curve cryptography, which could be easily broken by a quantum adversary. This is where PQC becomes essential. By integrating PQC algorithms into blockchain protocols, systems can become resistant to future quantum decryption capabilities.
For example:
- Quantum-safe digital signatures can replace traditional keys in user wallets.
- PQC-based identity verification can make decentralized identity systems more secure.
- Smart contracts can be encrypted with quantum-resistant algorithms, protecting them from tampering even in the quantum age.
By adopting PQC within blockchain architectures, we can preserve the immutability, decentralization, and transparency of blockchain, while upgrading its foundational security layer to resist next-generation threats.
Real-World Use Cases and Applications
Several initiatives are already exploring this intersection. For instance:
- The National Institute of Standards and Technology (NIST) is finalizing its recommendations for PQC algorithms, which can be incorporated into blockchain systems.
- Blockchain projects like QANplatform and IBM’s Quantum-Safe Blockchain are experimenting with hybrid architectures combining PQC with distributed ledger technologies.
In sectors like finance, healthcare, and supply chain, this dual-layered security approach could be pivotal. Financial transactions, medical records, and identity credentials stored on blockchain platforms could remain secure even decades into the quantum future.
Conclusion: A Secure Digital Future
As quantum computing inches closer to practical implementation, the urgency to transition to quantum-resistant systems grows. By merging Post-Quantum Cryptography with Blockchain technology, we create a secure foundation that not only resists today’s cyber threats but also anticipates the security challenges of tomorrow.
This convergence represents a critical leap forward for digital trust—one where users can confidently engage in online activities knowing their data and identity are protected not just for years, but for generations.
Connect with us : https://linktr.ee/bervice