As the era of quantum computing approaches, organizations relying on traditional Web2 infrastructures face a looming threat: quantum attacks capable of breaking today’s cryptographic systems. Unlike classical computers, quantum machines leverage quantum mechanics to solve certain problems exponentially faster — a capability that directly undermines the foundations of modern cybersecurity, especially public-key cryptography.
In this article, we explore the first practical steps developers, enterprises, and system administrators can take to prepare and fortify Web2 environments against this emerging quantum threat.
1. Understanding the Quantum Risk to Web2
Most of today’s internet communication relies on cryptographic algorithms like RSA, ECC (Elliptic Curve Cryptography), and DH (Diffie-Hellman) for key exchange, digital signatures, and encryption. These algorithms are considered secure because factoring large integers or solving discrete logarithm problems is infeasible for classical computers.
However, quantum algorithms like Shor’s algorithm can break these cryptosystems in polynomial time, rendering widely-used protocols like HTTPS, VPNs, TLS, and even blockchain signatures insecure. The risk is especially serious for long-lived data — for instance, encrypted medical or legal records that may still be sensitive when quantum computers become capable of decryption.
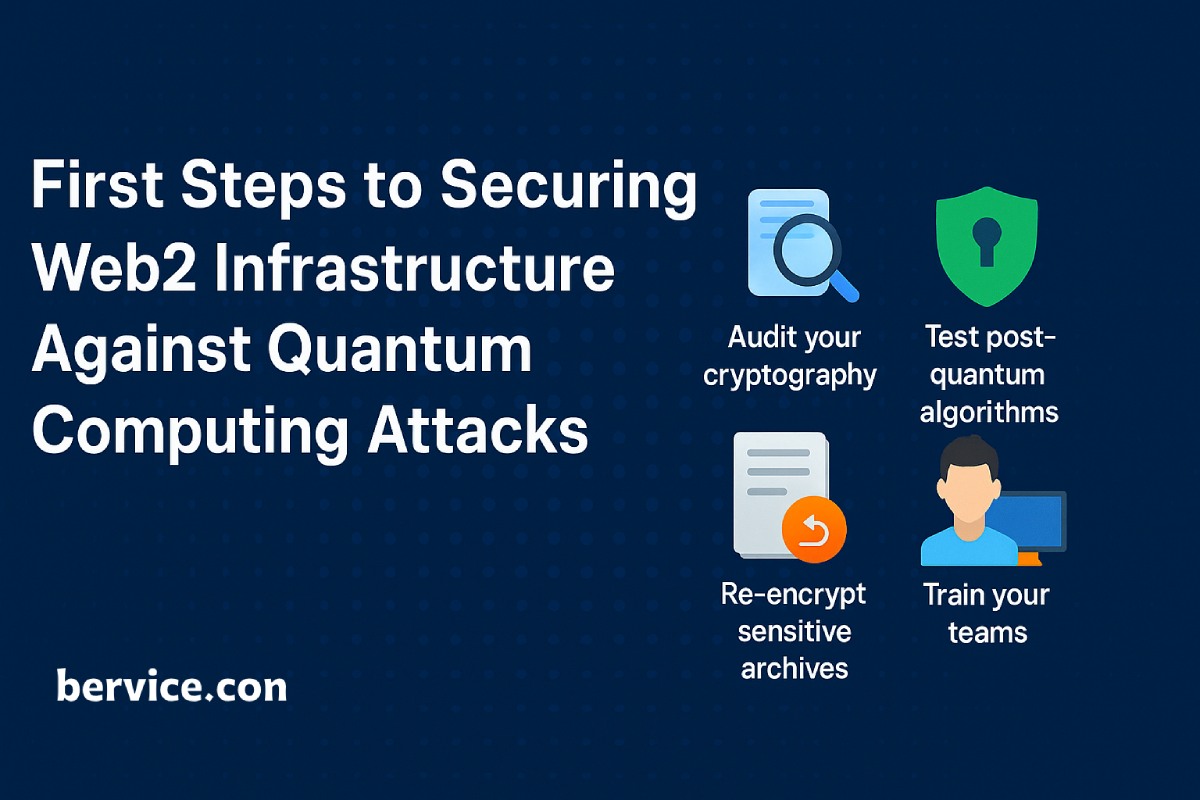
2. Inventory and Cryptographic Audit
The first step in defending against quantum threats is to identify and map all cryptographic assets within your Web2 infrastructure:
- What libraries are in use (e.g., OpenSSL, Bouncy Castle)?
- Which algorithms are used for transport (TLS), data encryption, authentication, and storage?
- What third-party services depend on cryptographic protocols?
This inventory helps determine which systems are at risk and require replacement or updating. It also highlights where sensitive data might be harvested today to be decrypted later in a “store now, decrypt later” attack.
3. Transition to Post-Quantum Cryptography (PQC)
Post-Quantum Cryptography refers to cryptographic algorithms believed to be secure against quantum attacks but still usable by classical systems. NIST is in the process of standardizing PQC algorithms, with finalists like:
- CRYSTALS-Kyber (key encapsulation)
- CRYSTALS-Dilithium (digital signatures)
- FALCON and SPHINCS+ (signature schemes)
Organizations should begin experimenting with these algorithms in parallel environments (hybrid deployments), where both classical and PQC algorithms are used. For instance, enabling hybrid TLS connections that combine ECC and PQC key exchange ensures backward compatibility while enhancing security.
4. Secure Key Management and Quantum-Resistant Protocols
In addition to upgrading cryptographic algorithms, organizations should review their key management practices:
- Use shorter key lifespans to limit long-term exposure.
- Rotate keys more frequently, especially for critical services.
- Deploy quantum-resistant key derivation functions (KDFs).
Developers should also watch evolving protocols such as Hybrid TLS 1.3, Signal PQ extensions, and VPNs with PQC support, and begin migrating as they mature.
5. Data-at-Rest and Forward Secrecy
Securing data in motion is critical, but so is data at rest. Long-term encrypted data, especially in backups and archives, must be evaluated for future decryptability.
- Use quantum-safe encryption for new storage.
- Where possible, implement perfect forward secrecy (PFS) to ensure compromise of one session key does not expose past communications.
- Consider re-encryption of old sensitive archives using PQ-safe methods.
6. Staff Training and Security Awareness
Quantum readiness is not purely technical. Teams must be educated on the implications of quantum threats, especially security architects, network engineers, and IT managers.
- Provide training on post-quantum principles and emerging standards.
- Involve the team in risk assessments and pilot migrations to PQC.
- Maintain clear documentation for all cryptographic changes.
7. Monitor Standards and Evolve Gradually
Quantum computers capable of breaking RSA/ECC at scale may be a few years away — but preparation must start now. NIST’s final PQC recommendations are expected soon, and organizations should follow developments closely.
Adopting a “crypto-agile” architecture is essential — systems must be designed to switch cryptographic algorithms as new threats emerge or standards evolve.
Conclusion: Prepare Today, Stay Secure Tomorrow
Quantum computing will profoundly reshape the cybersecurity landscape, but the threat is not a surprise — it’s a forecasted evolution. Web2 infrastructure, though rooted in classical systems, can be fortified with proactive measures. By auditing existing cryptography, experimenting with PQC, enhancing key management, and training staff, organizations can begin their journey toward a quantum-resilient digital future.
🔐 Quantum-safe today means trust tomorrow. The clock is ticking — the time to prepare is now.
Connect with us : https://linktr.ee/bervice