Introduction: The Quantum Threat to Classical Encryption
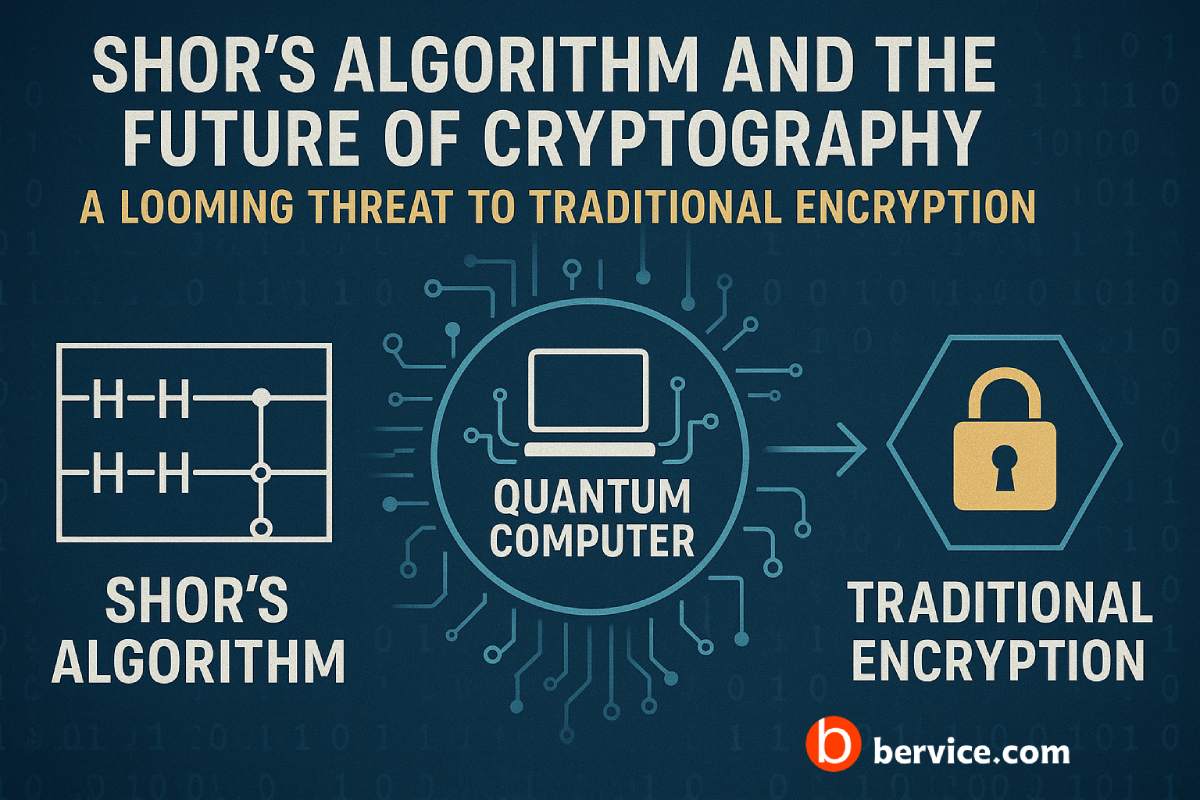
The rise of quantum computing is both a technological milestone and a looming threat to modern cryptography. Many encryption schemes that secure today’s digital systems — including AES, RSA, and ECC — are vulnerable to powerful quantum algorithms such as Shor’s and Grover’s. File encryption systems, which form the backbone of secure local and cloud storage, are especially at risk. Post-Quantum Cryptography (PQC) emerges as a crucial line of defense, designed to remain secure even against adversaries with access to quantum computers.
📂 Understanding the Vulnerability of File Encryption
File encryption systems typically rely on symmetric (e.g., AES) and asymmetric (e.g., RSA, ECC) algorithms to protect data. While AES is relatively resistant to quantum attacks (Grover’s algorithm only weakens it by half), asymmetric schemes suffer catastrophic vulnerabilities. For instance, Shor’s algorithm can efficiently factor large primes or compute discrete logs, rendering RSA and ECC completely insecure. This makes key exchanges, digital signatures, and hybrid encryption modes within file systems highly susceptible.
🔐 What Is Post-Quantum Cryptography?
Post-Quantum Cryptography refers to cryptographic algorithms that are designed to be secure against both classical and quantum computers. Unlike traditional public-key systems, PQC relies on hard mathematical problems such as:
- Lattice-based problems (used in Kyber, Dilithium)
- Hash-based signatures (SPHINCS+)
- Code-based cryptography (Classic McEliece)
- Multivariate polynomial problems
These schemes are considered infeasible to break even with a large-scale quantum computer, offering a quantum-resilient foundation for securing file systems.
🧩 How PQC Secures File Encryption Systems
Post-Quantum algorithms can be integrated into file encryption workflows in the following ways:
- Key Encapsulation Mechanism (KEM):
PQC KEMs (e.g., Kyber) can replace RSA/ECC in secure key exchange, ensuring that session keys used to encrypt files (with AES or ChaCha20) remain safe even in a post-quantum world. - Digital Signatures for File Integrity:
File storage often uses signatures to detect tampering. Replacing RSA or ECDSA with PQ-safe signatures (like Dilithium or SPHINCS+) ensures integrity remains verifiable in the quantum era. - Hybrid Encryption Schemes:
PQC can be used alongside traditional cryptography (e.g., AES + Kyber), combining the maturity of classical schemes with the resilience of quantum-safe alternatives. This approach allows smooth migration while ensuring future-proof security. - Zero-Trust and Decentralized Systems:
In decentralized storage or zero-trust environments, PQC enables trustless data sharing by securing identities and key exchanges without risking future compromise.
🧪 Real-World Implementation and Migration Strategies
Implementing PQC in file encryption systems requires thoughtful design:
- Backward Compatibility: Systems must support classical and PQC algorithms simultaneously during transition.
- Performance Optimization: Some PQC algorithms have larger key sizes and slower performance; choosing efficient algorithms like Kyber can mitigate this.
- Standardization: NIST’s PQC standardization project has finalized Kyber (encryption) and Dilithium (signature) as its first choices, enabling stable adoption in critical applications.
Projects like OpenSSH, Signal, and several VPNs have already started integrating PQC prototypes, and libraries such as liboqs provide developers with tools to experiment with post-quantum algorithms.
🔮 Conclusion: Quantum-Ready File Encryption Is No Longer Optional
The inevitability of quantum computing forces a re-evaluation of how we protect sensitive files — from corporate secrets to personal vaults. While quantum computers are not yet mainstream, the data encrypted today could be harvested and decrypted in the future (“Harvest Now, Decrypt Later” attacks). Transitioning to post-quantum cryptographic systems is the only proactive solution.
By embedding post-quantum mechanisms into file encryption — from key exchange to signatures — we ensure that the confidentiality, authenticity, and integrity of data remain intact, even in a future where quantum threats become reality.
Connect with us : https://linktr.ee/bervice