In an era defined by rapid digital transformation, the protection and transfer of sensitive information have emerged as critical concerns. As traditional cybersecurity systems struggle to keep pace with increasingly sophisticated threats, the convergence of blockchain technology, quantum computing, and decentralized storage is shaping the next generation of secure information infrastructure. These three powerful technologies are not just complementary—they are collectively paving the way for a paradigm shift in how data is encrypted, stored, and transmitted.
Blockchain: Trustless Security at the Core
Blockchain technology offers an immutable, transparent, and decentralized ledger that eliminates the need for third-party intermediaries. This trustless architecture ensures that data and transactions are cryptographically secured and verifiable by all participants. In secure communications, blockchain can validate the authenticity of messages, enforce digital rights, and power smart contracts for automated, tamper-proof exchanges.
Moreover, when combined with encryption layers, blockchain ensures that even if a message is intercepted, its contents remain unintelligible without the corresponding private key. This provides a foundational framework for secure information transfer in decentralized applications (dApps), digital identity verification, and cross-border digital transactions.
Quantum Computing: Redefining Cryptography and Threat Models
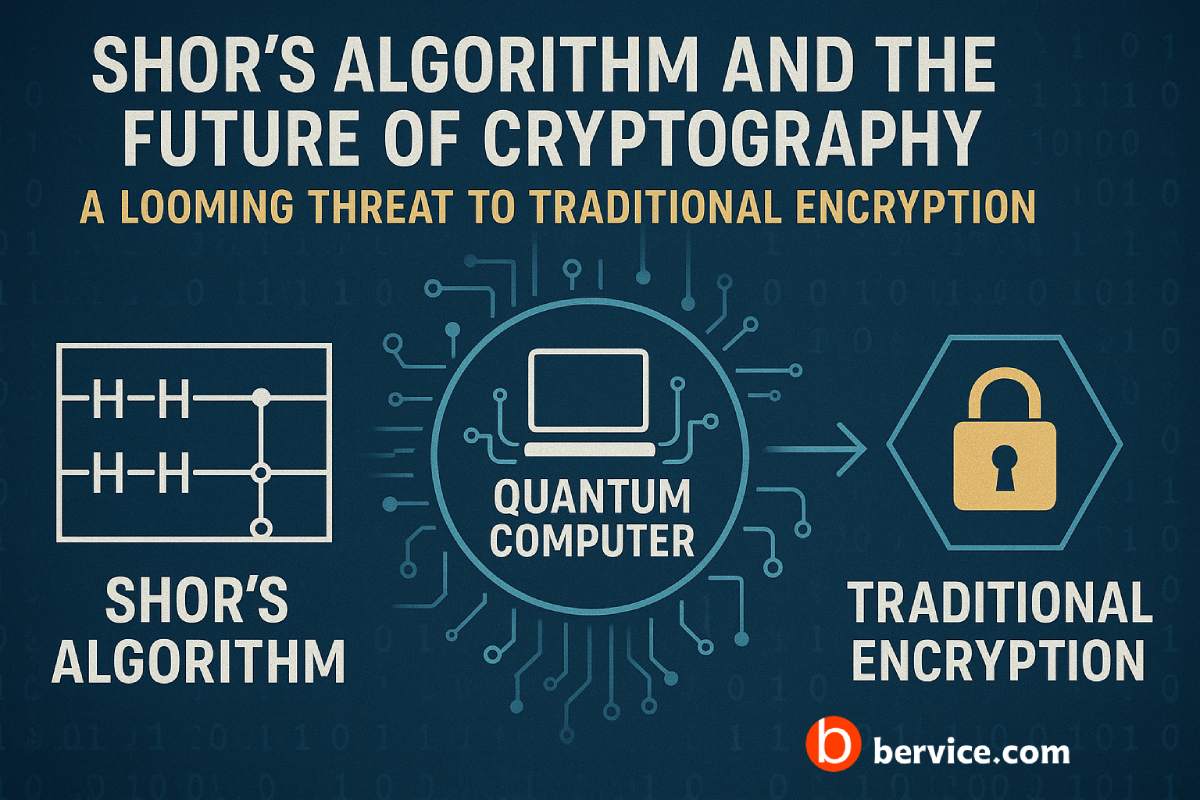
While quantum computing poses a potential threat to conventional encryption algorithms (e.g., RSA and ECC), it also offers unprecedented capabilities for generating truly random numbers, solving complex problems, and enabling quantum key distribution (QKD). QKD allows two parties to share cryptographic keys with security rooted in the laws of quantum mechanics—making it impossible for a third party to intercept without detection.
By integrating quantum-safe algorithms and post-quantum cryptography (PQC), we can ensure that data remains secure even in a future where quantum computers are mainstream. Blockchain networks and digital platforms must evolve to adopt these algorithms to maintain integrity and confidentiality in the quantum era.
Decentralized Storage: Eliminating Single Points of Failure
Traditional cloud storage systems are centralized, making them attractive targets for cyberattacks and vulnerable to data breaches, censorship, and server outages. Decentralized storage solutions such as IPFS, Arweave, and Filecoin distribute data across multiple nodes in a peer-to-peer network. This ensures that no single entity has full control over the data, increasing both privacy and availability.
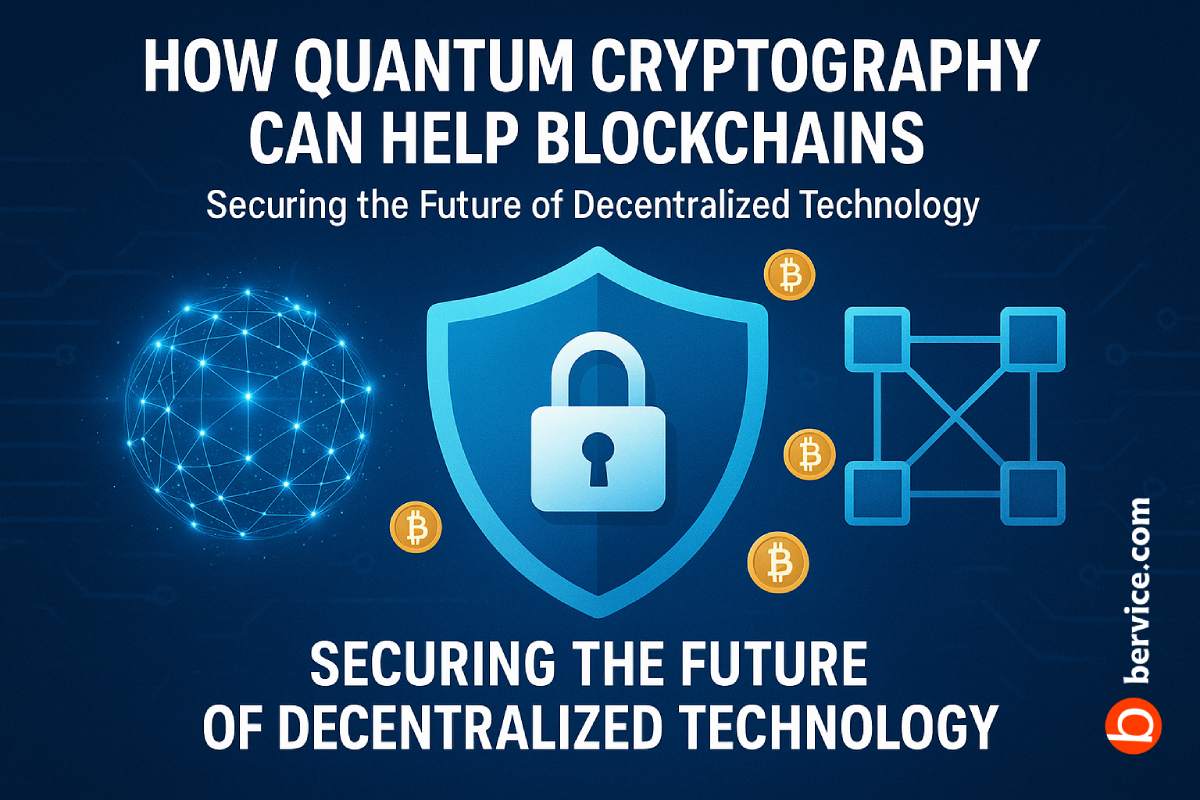
When combined with blockchain authentication and quantum-resistant encryption, decentralized storage offers a powerful architecture for hosting sensitive information—from personal identity documents to medical records and corporate archives.
The Synergy: A New Secure Digital Ecosystem
The real breakthrough lies in the synergy of these technologies. Imagine a future where:
- Data is encrypted using post-quantum cryptography
- Stored on decentralized, censorship-resistant platforms
- Transmitted and verified via smart contracts on a blockchain
- Secured further using quantum-based key exchange protocols
This holistic ecosystem will redefine digital trust, ensuring that data sovereignty, privacy, and resilience are not just ideals but practical realities.
Conclusion
The future of secure information is being forged today at the intersection of blockchain, quantum computing, and decentralized storage. Together, they hold the promise of building an internet that is safer, smarter, and fundamentally more equitable. As businesses, governments, and innovators adopt these technologies, they will unlock a new era of digital communication—one that empowers users, protects privacy, and withstands even the most advanced cyber threats.
Connect with us : https://linktr.ee/bervice